Typical LAN Topology

University Of Detroit Mercy
Virtual LANs
Instroctor: Dr. Nizar Alholou
Student: Hosam Amona
Virtual LAN Technology
Introduction:
Traditional Local Area Networks originally were developed for two main reasons: information sharing and resource sharing between users in the same organization. We can describe two basic types of LANs: a peer-to-peer LAN or a dedicated server LAN. Local Area Network is considered a single broadcast domain; a message from one computer can be seen by all computers in the LAN. Many reasons contributed to the congestion of traditional LANs. For example, routers in general are used to connect different LANs together, and normally they delay the transmission of data and generate unnecessary traffic. Also, the speed of the desktop PCs and work stations is increasing, operating systems are faster now than 10 years ago, and the use of network-intensive applications (e.g., client server applications) are very common now and rising. To solve the problem of the congested and overburden traditional LANs the technology of Virtual LAN was introduced which uses switches and other intelligent and advanced network devices instead of routers. The use of switches improve the performance of the LAN by creating isolated collision domains. Spreading the user over several segments of VLANs (and several collision domains) collision can be avoided and performance improves. Switches can assign a single user per port, which means one user will get 10 Mbps bandwidth.
Virtual LAN Technology
What is a Virtual LAN?
Virtual LANs (or logical) LANs can be defined as a group of workstations and network devices, or physical LANs segments which are grouped to communicate together regardless of their physical locations. Different strategies are used to group these workstations together in a VALN. For example, they can be grouped according to the users' activities, departmental functions, or any other criteria except geographical locations. As described before, the segmentation of the network is done logically and not physically. Generally, VLAN can be considered as a broadcast domain, which means packets are only switched between ports of the same VLAN and traffic is contained within the intended VLAN.
Typical LAN Topology 
Virtual LAN Technology
Implementation of a Virtual LAN
They are several ways to implement and define the end-user membership in a VLAN. According to that VLANs can be divided into five general types:
Membership by Switch Port Group:
The initial implementations of a VLAN, a groups of switch ports will make up a VLAN (for example, ports 2,3,5 and 8 will make up VLAN A, while ports 1,4,6 and 7 make up VLAN B). An other generation of VLANs was implemented by grouping together several ports from different switches (for example port 2 and 5 from switch number 1 and port 1, 3, and 6 from switch number 2 make up VLAN A, while port 1,3, and 6 from switch number 1 and port 2, 4,7, and 8 from switch number 2 make up VLAN B). This is the most common method in defining and implementing a VLAN. The only limitation for this method is that, the network manager has to reconfigure the VLAN membership every time a user moves from one port to another.

Virtual LAN Technology
Membership by MAC Address:
The MAC-layer address for each workstation is in the network interface card (NIC). This allows network managers to move a workstation to a different location, so the user membership remain the same. This method require that all users in the network must be configured initially in at least one VLAN. The result of this initial configuration is that thousands of users will be assigned to the same VLAN. A serious performance degradation is the biggest disadvantage of this initial configuration. Another limitation to this method arise when an organization uses a significant numbers of laptops. The MAC address is in the docking station, so every time a laptop is moved to a different docking station, the VLAN membership has to be updated.
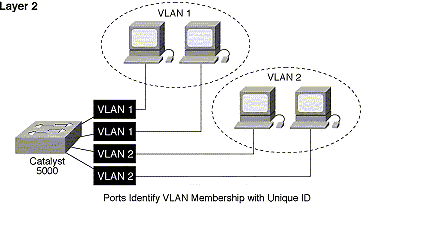
Virtual LAN Technology
Membership by Network Layer Information:
These types of VLANs (also known as layer-3 base VLAN) take into consideration the protocol type. The switch inspect the packet's IP address and then determine the VLAN membership of the particular workstation. We should note here that this process does not become a routing process. Defining a VLAN based on layer 3 information have several advantages:
The only limitation for this method is its performance due to the slow process of inspecting layer 3 addresses packets. VLAN defined at layer 3 was found to be more effective with protocol such as TCP/IP and less effective with protocols like IPX, 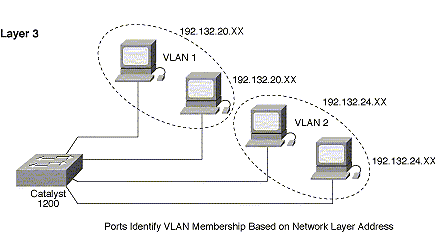 DECnet, and AppleTalk.
DECnet, and AppleTalk.
Figure 4 Layer 3 VLAN
Virtual LAN Technology
IP Multicast Group:
workstations can be joined together as an IP multicast group. These groups of IPs are established dynamically. The workstation will be given a chance to join the IP multicast group for a certain period of time. Therefore, a VLAN is established for each IP multicast group, and when a packet is sent it will directed to the specific group of IP addresses. This method of defining VLANs has a very high degree of flexibility and application sensitivity.
Higher Layer VLAN:
Membership of another type of VLAN can be defined based on applications or services, or a combination of both. For example, File Transfer Protocol (FTP) applications can be processed together in one VLAN, and Telnet applications on another VLAN. This type of VLAN creates more complex VLANs to manage and need a high level of automated configuration features.

Virtual LAN Technology
Advantages of a VLAN
There are so many benefits for Virtual LANs for the end-user and the network managers. We can identify the following as the most important:
Virtual LAN Technology

GUI-type Switch Management Software

Virtual LAN Technology
The Proposed Standards of Virtual LAN:
Switches and VLAN products come from different venders, therefore each vender have developed their own proprietary VLAN products. Customers are forced now to buy from a single vender to avoid incompatibility. decision of implementing a VLAN solution should be considered part of the organization strategy. Venders that support VLANs equipment include Cisco, IBM, Bay Network, Alntec/FORE and 3Com.
The proposed VLAN standards are:
IEEE 802.10 "VLAN Standard" Proposed by Cisco Systems in 1995.
IEEE 802.1 Internetworking Subcommittee, 1996.
IEEE 802.1Q This will enables equipment from different venders to work together.
Virtual LANs
This chapter describes virtual LAN (VLAN) features and functionality, the Virtual LAN Menu of the Catalyst
1900 and Catalyst 2820 switches, and procedures for creating VLANs and assigning ports to VLANs.VLAN Description
A VLAN is a switched network that is logically segmented by functions, project teams, or applications without regard to the physical location of users. For example, several end stations might be grouped as a department, such as engineering or accounting. When the end stations are physically located close to one another, you can group them into a LAN segment. If any of the end stations are in different buildings (not the same physical LAN segment), you can then group them into a VLAN.
You can assign each switch port to a VLAN. Ports in a VLAN share broadcast traffic. Ports that do not belong to that VLAN do not share the broadcast traffic. Ports from multiple Catalyst
1900 and Catalyst 2820 switches can be members of the same VLAN. Figure 2-1 shows an example of VLANs that span multiple switches and multiple floors or a building.Figure
2-1: VLANs Spanning Multiple Switches and Multiple Floors
Features
VLANs provide the following features:
When an end station is physically moved to a new location, its attributes can be reassigned from a network management station through Simple Network Management Protocol (SNMP) or through the user interface menus. When an end station is moved within the same VLAN, it retains its previously assigned attributes in its new location. When an end station is moved to a different VLAN, the attributes of the new VLAN are applied to the end station.
You can assign the Internet Protocol (IP) address of a switch to any VLAN. A network management station and workstations on any Catalyst series switch VLAN then have direct access to other Catalyst 1900 and Catalyst 2820 switches on the same VLAN, without needing a router. Only one IP address can be assigned to a switch; if the IP address is reassigned to a different VLAN, the previous IP address assignment to a VLAN is invalid.
VLANs allow ports on the same or different switches to be grouped so that traffic is confined to members of only that group. This feature restricts broadcast, unicast, and multicast traffic (flooding) only to ports included in a certain VLAN. The management domain is a group of VLANs that are managed by a single administrative authority. From a single switch, you can create VLANs for an entire management domain.
You can increase security by segmenting the network into distinct broadcast domains. To this end, VLANs can restrict the number of users in a broadcast domain. You can also control the size and composition of the broadcast domain by controlling the size and composition of a VLAN.
Table 2-1 shows the capabilities and defaults for the Catalyst 1900 and Catalyst 2820 series VLAN features.
|
|
Capability |
Default |
|
Trunk ports |
Supports a maximum of two trunks. The Catalyst 1900 switch supports a maximum of two Inter-Switch Link (ISL) trunks. The Catalyst 2820 switch supports both ISL and Asynchronous Transfer Mode (ATM) LAN emulation (LANE) trunk connections and ATM permanent virtual connections (PVCs). Fast Ethernet trunk ports can be grouped using the Fast EtherChannel feature to form a single trunk. |
No trunk ports are enabled. |
|
Load sharing |
Supports Spanning-Tree Protocol (STP) on VLAN trunks to load share. |
No load sharing is set up. |
|
VLAN Trunk Protocol (VTP) |
Supports server, client, and transparent modes. Server and transparent modes support a maximum of 128 VLANs. From server mode, the switch automatically transitions to client mode if it learns more than 128 VLANs from advertisements. Client mode supports 1005 VLANs. |
Configured to server mode. Set to no-management domain state. |
|
VTP pruning |
Supports pruning. |
Pruning is disabled. |
|
VLAN membership |
Supports dynamic and static ports. |
The default VLAN membership of all ports is static, and all ports reside in VLAN 1. |
|
VLAN Membership Policy Server (VMPS) |
Does not function as a VMPS on the network. (The Catalyst 5000 series switches support this feature.) |
No default. |
|
STP |
Runs on a maximum of 64 VLANs at one time. |
VLANs 1 to 64 are enabled with STP. |
Components
Networks that have VLANs contain one or more of the following components:
Switches are the entry points into the switched fabric for end-station devices and can group users, ports, or logical addresses into common communities of interest.
You can use both a single switch or multiple connected switches to group ports and users into communities. By grouping ports and users together across multiple switches, VLANs can span single-building infrastructures, interconnected buildings, or campus networks.
Switches use frame identification, or tagging, to logically group users into administratively defined VLANs. Based on rules you define, tagging determines where the frame is to be sent by placing a unique identifier in the header of each frame before it is forwarded throughout the switch fabric. The identifier is examined and understood by each switch prior to any broadcasts or transmissions to other switches, routers, or end-station devices. When the frame exits the switch fabric, the switch removes the identifier before the frame is transmitted to the target end station.
You can logically group users on Ethernet and ATM networks by mapping VLANs on the Ethernet network to emulated LANs (ELANs) on the ATM network.
Routers provide policy-based control, broadcast management, and route processing and distribution. They also provide the communication between VLANs and the access to shared resources, such as servers and hosts. Routers connect to other parts of the network that are either logically segmented into subnets or that require access to remote sites across wide area links. Routers are integrated into the switching fabric by using high-speed backbone connections over Fast Ethernet links, FDDI, or ATM for higher throughput between switches and routers.
The VLAN transport protocol enables information to be exchanged between interconnected switches residing on the corporate backbone.
The backbone acts as the aggregation point for high-volume traffic. It also carries end-user VLAN information and identification between switches, routers, and directly attached servers. Within the backbone, high-bandwidth, high-capacity links carry the traffic throughout the enterprise.
VLANs provide compatibility with previously installed systems, such as shared hubs and stackable devices. You can add shared hubs without changing existing network equipment. You also can share traffic and network resources that attach directly to switching ports with VLAN designations.
VLAN Configuration Tasks
Use the Virtual LAN Menu to perform the following tasks, which are described in this chapter:
Accessing the Virtual LAN Menu
To access the Virtual LAN Menu, enter [V] Virtual LAN at the selection prompt on the Main Menu. The following display appears:
Catalyst 1900 - Virtual LAN Configuration
--------------------Information----------------
VTP version: 1
Configuration revision: 1
Maximum VLANs supported locally: 1005
Number of existing VLANs: 6
Configuration last modified by: 0.0.0.0 at 01-03-2000 18:35:56
--------------------Settings------------------
[N] Domain name
[V] VTP mode control Server
[F] VTP pruning mode Disabled
[O] VTP traps Enabled
--------------------Actions-------------------
[L] List VLANs [A] Add VLAN
[M] Modify VLAN [D] Delete VLAN
[E] VLAN Membership [S] VLAN Membership Servers
[T] Trunk Configuration [W] VTP password
[P] VTP Statistics [X] Exit to Main Menu
Enter Selection:
When configuring the functions displayed on the menu, you might not use the options in the order in which they appear in the menu. Many of the menu entries prompt you for an additional selection and then return you to the Virtual LAN Menu for the next step.
Management Domains
When creating a VLAN, you must first determine and configure the management domain on the switch. Management domains group VLANs into zones of different administrative responsibilities. Catalyst
1900 and Catalyst 2820 switches support only one management domain for each switch.Catalyst
1900 and Catalyst 2820 switches operate in one of three modes: server, client, or transparent mode. By default, a switch in the no-management domain state is a VTP server; that is, it learns from received advertisements on a configured trunk port. If trunks are configured on the switch, VTP receives and transmits VLAN advertisements. From the server mode, you can add or delete VLANs by using the VTP Management Information Base (MIB) SNMP management station, the command-line interface (CLI), or the console menus.A switch configured in VTP server mode advertises VLAN configuration to neighboring switches through its trunks and learns new VLAN configurations from those neighbors. Use the server mode to add or delete VLANs and to modify VLAN information by using the VTP MIB, the CLI, or the console menus. For example, when you add a VLAN, VTP advertises the new VLAN to other switches, and both servers and clients prepare to receive traffic on their trunk ports.
The Catalyst
1900 and Catalyst 2820 switches automatically change from VTP server mode to VTP client mode when they receive an advertisement with more than 128 VLANs. You cannot configure a Catalyst 1900 or Catalyst 2820 switch for VTP client mode. As in VTP server mode, a switch in VTP client mode also transmits advertisements and learns new information from advertisements. However, you cannot add, delete, or modify a VLAN through the MIB or the console. The VTP client does not maintain VLAN information in nonvolatile storage; when it starts, it learns the configuration by receiving advertisements from the trunk ports.In VTP transparent mode, the switch does not advertise or learn VLAN configurations from the network. When a switch is in VTP transparent mode, you can modify, add, or delete VLANs through the console menus, the CLI, or the MIB.
When a switch is in the no-management domain state and running in either server or client mode, it inherits a management domain name and configuration revision number upon receiving an advertisement from a configured trunk port. The configuration revision number reflects the latest revision of the VTP configuration. If a management domain for the switch is defined, the switch ignores advertisements with a different management domain or a lower configuration revision number and checks all received advertisements with the same management domain for consistency. If the information contained in the received advertisement is consistent, the switch propagates the advertisements to other trunk ports and adds the newly learned information locally. Because all devices in the same management domain learn about any new VLANs configured in the transmitting device, you need to configure a new VLAN on only one device in the management domain.
VLAN Characteristics
To create a new VLAN, you need to define the VLAN characteristics. The Enterprise Edition software prompts you to define these characteristics:
Note
When configuring an ATM module as a trunk port, each VLAN must be either mapped to a LANE client or bound to one or multiple PVCs. In each case, you specify the VLAN number when you create a LANE client or a PVC on the ATM module. For more information on configuring LANE clients, refer to the Catalyst 2820 ATM Modules Installation and Configuration Guide.
Summary:
The performance of traditional LANs can be improved using VLAN technology. The costly wiring upgrades, time-consuming host reconfiguration, use of routers, and other management issues are not part of the VLAN technology. The improved performance and the increased level of security can not be ignored and many organizations would like have these features in their network. the implementation of VLANs will achieve those goals. VLAN remains a single-vender solution due to the lack of standardization